1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
|
---
stage: Software Supply Chain Security
group: Authentication
info: To determine the technical writer assigned to the Stage/Group associated with this page, see https://handbook.gitlab.com/handbook/product/ux/technical-writing/#assignments
---
# Credentials inventory for GitLab self-managed
DETAILS:
**Tier:** Ultimate
**Offering:** Self-managed
As a GitLab administrator, you are responsible for the overall security of your instance.
To assist, GitLab provides an inventory of all the credentials that can be used to access
your self-managed instance.
This page describes how to manage the credentials inventory for GitLab self-managed. To manage credentials on GitLab.com, see [Credentials inventory for GitLab.com](../user/group/credentials_inventory.md).
In the credentials inventory, you can view all:
- Personal access tokens (PATs).
- Project access tokens
- Group access tokens ([introduced](https://gitlab.com/gitlab-org/gitlab/-/merge_requests/102959) in GitLab 15.6).
- SSH keys.
- GPG keys.
You can also [revoke](#revoke-a-users-personal-access-token), [delete](#delete-a-users-ssh-key), and view:
- Who they belong to.
- Their access scope.
- Their usage pattern.
- When they:
- Expire.
- Were revoked.
## Revoke a user's personal access token
You can revoke a user's personal access token.
1. On the left sidebar, at the bottom, select **Admin**.
1. Select **Credentials**.
1. By the personal access token, select **Revoke**.
If a **Revoke** button is not available, the token may be expired or revoked, or an expiration date set.
| Token state | Revoke button displayed? | Comments |
|-------------|--------------------------|----------------------------------------------------------------------------|
| Active | Yes | Allows administrators to revoke the PAT, such as for a compromised account |
| Expired | No | Not applicable; token is already expired |
| Revoked | No | Not applicable; token is already revoked |
When a PAT is revoked from the credentials inventory, the instance notifies the user by email.

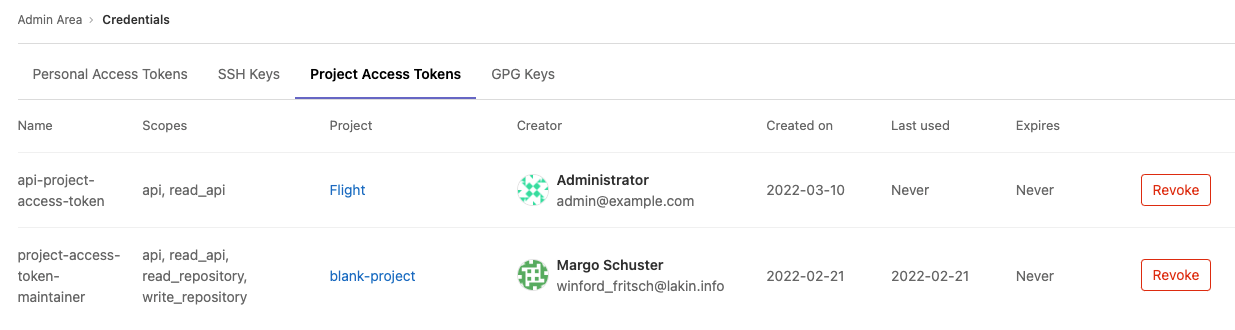
## Revoke a user's project access token
1. On the left sidebar, at the bottom, select **Admin**.
1. Select **Credentials**.
1. Select the **Project access tokens** tab.
1. By the project access token, select **Revoke**.
The project access token is revoked and a background worker is queued to delete the project bot user.
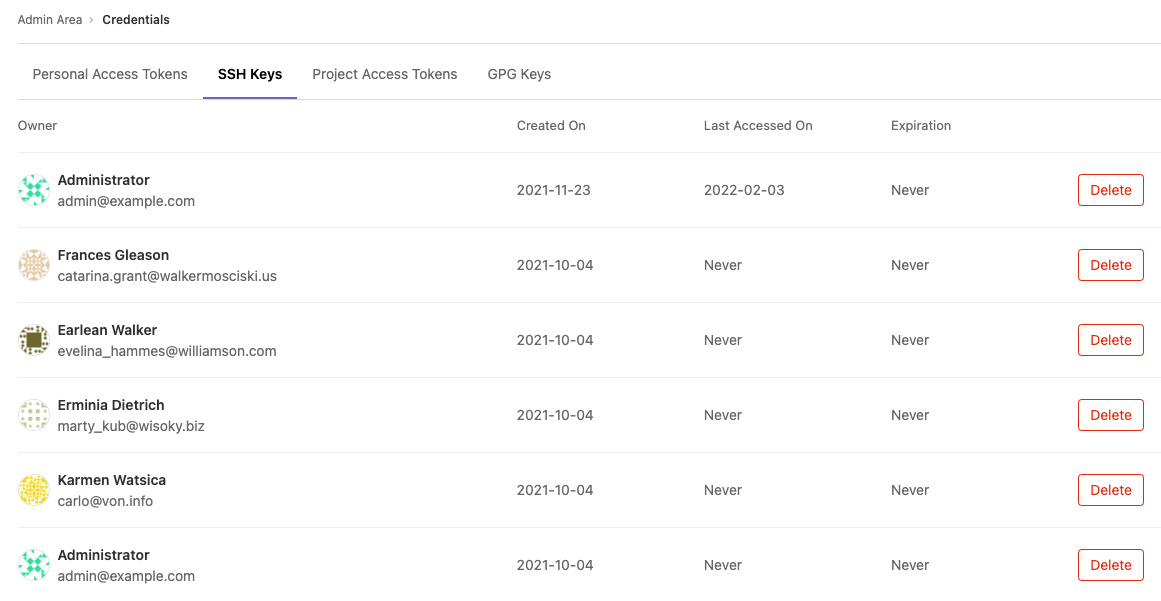
## Delete a user's SSH key
1. On the left sidebar, at the bottom, select **Admin**.
1. Select **Credentials**.
1. Select the **SSH Keys** tab.
1. By the SSH key, select **Delete**.
The instance notifies the user.
## Review existing GPG keys
You can view all existing GPG in your GitLab instance by going to the
credentials inventory GPG Keys tab, as well as the following properties:
- Who the GPG key belongs to.
- The ID of the GPG key.
- Whether the GPG key is [verified or unverified](../user/project/repository/signed_commits/gpg.md).

|